To create new wiki account, please join us on #znc at Libera.Chat and ask admins to create a wiki account for you. You can say thanks to spambots for this inconvenience.
Reverse Proxy: Difference between revisions
>Thor77 m Thor77 moved page Reverse proxy to Reverse Proxy over redirect |
|||
| (21 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
== About Reverse Proxies == | |||
While ZNC is a fantastic bouncer, in many situations it can be beneficial to utilize a reverse proxy in front of it for features such as: | |||
* Subdomains | |||
<nowiki>TrustedProxy = 127.0.0.1 | * Tighter control of SSL ciphers and protocols | ||
* ECDH support | |||
* SSL session caching | |||
* SSL stapling | |||
* Compression | |||
=== Notes === | |||
* <code>TrustedProxy</code> must be set in your configuration for web access logs to reflect actual addresses instead of the reverse proxy address (<code>127.0.0.1</code> / <code>::1</code>): | |||
<nowiki> | |||
TrustedProxy = 127.0.0.1 | |||
TrustedProxy = ::1</nowiki> | TrustedProxy = ::1</nowiki> | ||
== Nginx == | == Nginx == | ||
'''Note:''' If you plan on utilizing Nginx for IRC in conjunction with HTTP/HTTPS, the port number (''or'' address) of the two services '''must be different'''. | |||
=== HTTP === | |||
==== As a Subdomain ==== | |||
<nowiki>server { | <nowiki>server { | ||
listen 80; | listen 80; | ||
listen [::]:80; | listen [::]:80; | ||
server_name znc. | # To listen on a specific address only: | ||
# listen 192.0.2.1:80; | |||
# listen [2001:db8::192:0:2:1]:80; | |||
server_name znc.example.test; | |||
access_log /var/log/nginx/znc.example.test/znc-access.log; | |||
error_log /var/log/nginx/znc.example.test/znc-error.log; | |||
location / { | location / { | ||
proxy_pass http://[::1]:6667/; | |||
# For IPv4 loopback (there's almost no reason to do this) | |||
# proxy_pass http://127.0.0.1:6667/; | |||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; | |||
} | |||
}</nowiki> | |||
==== As a Subdirectory ==== | |||
'''Note:''' | |||
* There is intentionally no <code>/</code> after the port number | |||
* You must set <code>URIPrefix</code> of the Listener in ZNC to the target location (<code>/znc/</code> in this example) | |||
<nowiki>server { | |||
... | |||
location /znc/ { | |||
proxy_pass http://[::1]:6667; | |||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; | |||
} | |||
}</nowiki> | |||
On most distributions this would be put in <code>/etc/nginx/conf.d/znc.example.test.conf</code> . | |||
=== HTTPS === | |||
This is a basic configuration utilizing Diffie Hellman key exchange: | |||
<nowiki> | |||
server { | |||
listen 7001 ssl http2; | |||
listen [::]:7001 ssl http2; | |||
# To listen on a specific address only: | |||
# listen 192.0.2.1:7001 ssl http2; | |||
# listen [2001:db8::192:0:2:1]:7001 ssl http2; | |||
server_name znc.example.test; | |||
access_log /var/log/nginx/znc.example.test/znc_ssl-access.log; | |||
error_log /var/log/nginx/znc.example.test/znc_ssl-error.log; | |||
# SSL options | |||
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always; | |||
ssl_certificate /etc/letsencrypt/live/znc.example.test/fullchain.pem; | |||
ssl_certificate_key /etc/letsencrypt/live/znc.example.test/privkey.pem; | |||
ssl_dhparam /etc/letsencrypt/live/znc.example.test/dhparam.pem; | |||
ssl_trusted_certificate /etc/letsencrypt/live/znc.example.test/chain.pem; | |||
location / { | |||
proxy_pass http://[::1]:7001$uri; | |||
# For IPv4 loopback (there's almost no reason to do this) | |||
# proxy_pass http://127.0.0.1:7001$uri; | |||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; | proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; | ||
} | } | ||
}</nowiki> | }</nowiki> | ||
On most distributions this would be put in <code>/etc/nginx/conf.d/znc.example.test.conf</code> . | |||
=== IRC === | |||
Nginx has a directive separate from <code>http</code> called [https://nginx.org/en/docs/stream/ngx_stream_core_module.html stream] for protocols other than HTTP. We can utilize this to allow nginx to act as a reverse proxy for ZNC: | |||
<nowiki> | |||
upstream znc { | |||
server [::1]:7000; | |||
# For IPv4 loopback (there's almost no reason to do this) | |||
# server 127.0.0.1:7000; | |||
} | |||
server { | |||
listen 7000 ssl; | |||
listen [::]:7000 ssl; | |||
# To listen on a specific address only: | |||
# listen 192.0.2.1:7000 ssl; | |||
# listen [2001:db8::192:0:2:1]:7000 ssl; | |||
# SSL options | |||
ssl_certificate /etc/letsencrypt/live/znc.example.test/fullchain.pem; | |||
ssl_certificate_key /etc/letsencrypt/live/znc.example.test/privkey.pem; | |||
ssl_dhparam /etc/letsencrypt/live/znc.example.test/dhparam.pem; | |||
ssl_trusted_certificate /etc/letsencrypt/live/znc.example.test/chain.pem; | |||
proxy_pass znc; | |||
}</nowiki> | |||
On most distributions these would be put in <code>/etc/nginx/conf.d/znc.example.test.stream</code> . | |||
=== Additional Configuration Abilities === | |||
Nginx has many configuration options that can enhance the behavior of both the ZNC web interface and IRC, so the <code>http</code> or <code>server</code> nginx directive options below only demonstrate the most common portions of them: | |||
<nowiki> | |||
sendfile on; | |||
tcp_nopush on; | |||
tcp_nodelay on; | |||
keepalive_timeout 65; | |||
types_hash_max_size 2048; | |||
server_tokens off; | |||
# Compression | |||
gzip on; | |||
gzip_comp_level 9; | |||
gzip_types application/javascript application/vnd.ms-fontobject application/x-font-otf application/x-font-ttf application/x-font-woff image/jpg image/png image/svg image/x-icon text/css; | |||
############### | |||
# SSL options # | |||
############### | |||
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:DHE-DSS-AES256-GCM-SHA384:DHE-DSS-AES256-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256; | |||
ssl_ecdh_curve secp384r1; | |||
ssl_protocols TLSv1.2 TLSv1.3; | |||
ssl_prefer_server_ciphers on; | |||
ssl_session_cache shared:https:15m; | |||
ssl_session_timeout 15m; | |||
# Stapling | |||
ssl_stapling on; | |||
ssl_stapling_verify on; | |||
resolver 1.1.1.1 8.8.8.8 [2606:4700:4700::1111] [2001:4860:4860::8888]; | |||
</nowiki> | |||
== lighttpd == | == lighttpd == | ||
=== HTTP === | |||
<nowiki>$HTTP["host"] =~ "^(sub\.domain\.com)$" { | <nowiki>$HTTP["host"] =~ "^(sub\.domain\.com)$" { | ||
proxy.server = ( "" => ( ( "host" => "127.0.0.1", "port" => 6667 ) ) ) | proxy.server = ( "" => ( ( "host" => "127.0.0.1", "port" => 6667 ) ) ) | ||
}</nowiki> | }</nowiki> | ||
== Traefik == | |||
It is possible to run ZNC as a docker container, and use [https://traefik.io/ Traefik] to provide proxying services for this. The IRC port needs to be separated from the web interface port to achieve this. | |||
=== Traefik setup === | |||
Traefik needs to be configured to listen on a specific port for IRC access to ZNC. In this example, I'm using port 7000 for 'web' based access, and 7001 for 'IRC' access. This can be done in docker-compose as follows: | |||
<pre> | |||
version: "3.5" | |||
networks: | |||
default: | |||
name: traefik | |||
services: | |||
traefik: | |||
image: "traefik:v2.3" | |||
command: | |||
--entryPoints.web.address=:7000 | |||
--entryPoints.irc.address=:7001 | |||
--providers.docker=true | |||
ports: | |||
- "7000:7000" | |||
- "7001:7001" | |||
</pre> | |||
=== ZNC setup === | |||
ZNC also needs to be configured to allow a separate port for IRC access. In this example, I'm using port 6501 for web access, and 6502 for IRC access. This is configured as follows: | |||
[[File:Znc-ports-traefik.png|center|ZNC Port Configuration]] | |||
The ZNC docker container then needs to be configured with appropriate labels to configure traefik to send traffic to it. This can be done in docker-compose as follows (in this case, the host name 'znc.example.com' is being used to access the ZNC service): | |||
<pre> | |||
--- | |||
version: "3.5" | |||
networks: | |||
traefik: | |||
external: true | |||
default: | |||
name: znc | |||
services: | |||
znc: | |||
image: znc | |||
container_name: znc | |||
volumes: | |||
- ./zncconfig:/znc-data | |||
networks: | |||
- default | |||
- traefik | |||
ports: | |||
- 6501:6501 | |||
- 6502:6502 | |||
restart: unless-stopped | |||
labels: | |||
- "traefik.enable=true" | |||
- "traefik.http.routers.zncweb.rule=Host(`znc.example.com`)" | |||
- "traefik.http.routers.zncweb.tls=true" | |||
- "traefik.http.routers.zncweb.entryPoints=web" | |||
- "traefik.http.services.zncweb.loadbalancer.server.port=6501" | |||
- "traefik.tcp.routers.zncirc.rule=HostSNI(`znc.example.com`)" | |||
- "traefik.tcp.routers.zncirc.tls=true" | |||
- "traefik.tcp.routers.zncirc.entryPoints=irc" | |||
- "traefik.tcp.services.zncirc.loadbalancer.server.port=6502" | |||
- "traefik.docker.network=traefik" | |||
</pre> | |||
=== IRC client setup === | |||
All that is required then is to configure your IRC client to connect securely to 'znc.example.com' on port 7001, with SSL enabled. Traefik will then provide the appropriate certificate for the connection, and pass traffic to port 6502 on the ZNC container. | |||
=== ZNC web control panel === | |||
The ZNC web control panel can be accessed using (in this case) <code>https://znc.example.com:7000/</code> | |||
== Caddy == | |||
[https://caddyserver.com/ Caddy] is an extensible, cross-platform, open-source web server written in Go, with automatic TLS certificate provisioning. | |||
Caddy only supports reverse proxying for HTTP out of the box, but the [https://github.com/mholt/caddy-l4 caddy-l4] plugin allows Caddy to proxy arbitrary streams, which makes it useful for ZNC. When using Caddy in this mode, the web control panel and IRC can be served from a single port. | |||
Build Caddy with the caddy-l4 plugin by following the directions in caddy-l4's README. | |||
caddy-l4 is configured by adding a `layer4` object to the `apps` object of a JSON Caddy configuration, like the one below. Note that the comments must be removed. | |||
<nowiki> | |||
{ | |||
"apps": { | |||
"layer4": { | |||
"servers": { | |||
"znc": { | |||
"listen": [ | |||
":1337" // Caddy will listen on this interface | |||
], | |||
"routes": [ | |||
{ | |||
"handle": [ | |||
{ | |||
// Terminate TLS | |||
"handler": "tls", | |||
"connection_policies": [ | |||
{ | |||
"alpn": [ | |||
// Caddy always tries to negotiate HTTP/2 by default, | |||
// which ZNC's web interface doesn't support, so we need | |||
// to override the default protocol list | |||
"http/1.1", | |||
"http/1.0" | |||
], | |||
// Some IRC clients don't support SNI negotiation, so you | |||
// need to tell Caddy which certificate to send | |||
"default_sni": "your.hostname.com" | |||
} | |||
] | |||
}, | |||
{ | |||
// Forward cleartext to ZNC | |||
"handler": "proxy", | |||
"upstreams": [ | |||
{ | |||
"dial": [ | |||
"localhost:2337" // The address where ZNC is listening | |||
] | |||
} | |||
] | |||
} | |||
] | |||
} | |||
] | |||
} | |||
} | |||
} | |||
} | |||
} | |||
</nowiki> | |||
== Apache == | |||
* You need the <code>proxy_http</code> and <code>rewrite</code> modules to be enabled. On Ubuntu you can do <code>a2enmod proxy_http rewrite</code> and then restart yor Apache instance. | |||
=== HTTP === | |||
==== As a Subdomain ==== | |||
* The ZNC web control panel can be accessed using (in this case) <code>http://znc.example.com/</code> | |||
<pre> | |||
<VirtualHost *:80> | |||
ServerName znc.example.com | |||
ServerAdmin webmaster@localhost | |||
DocumentRoot /var/www/html/znc | |||
ErrorLog ${APACHE_LOG_DIR}/znc-error.log | |||
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined | |||
<Location /> | |||
ProxyPass http://localhost:1337/ | |||
ProxyPassReverse http://localhost:1337/ | |||
</Location> | |||
</VirtualHost> | |||
</pre> | |||
==== As a Subdirectory ==== | |||
* You must set <code>URIPrefix</code> of the Listener in ZNC to the target location (<code>/znc/</code> in this example) | |||
* The ZNC web control panel can be accessed using (in this case) <code>http://znc.example.com/znc/</code> | |||
<pre> | |||
<VirtualHost *:80> | |||
ServerName znc.example.com | |||
ServerAdmin webmaster@localhost | |||
DocumentRoot /var/www/html/znc | |||
ErrorLog ${APACHE_LOG_DIR}/znc-error.log | |||
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined | |||
<Location /znc> | |||
ProxyPass http://localhost:1337/znc | |||
ProxyPassReverse http://localhost:1337/znc | |||
</Location> | |||
</VirtualHost> | |||
</pre> | |||
=== HTTPS === | |||
==== As a Subdomain ==== | |||
* The ZNC web control panel can be accessed using (in this case) <code>https://znc.example.com/</code> | |||
<pre> | |||
<IfModule mod_ssl.c> | |||
<VirtualHost *:443> | |||
ServerName znc.example.com | |||
ServerAdmin webmaster@localhost | |||
DocumentRoot /var/www/html/znc | |||
ErrorLog ${APACHE_LOG_DIR}/znc-error.log | |||
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined | |||
Include /etc/letsencrypt/options-ssl-apache.conf | |||
<Location /> | |||
ProxyPass http://localhost:4447/ | |||
ProxyPassReverse http://localhost:4447/ | |||
</Location> | |||
SSLCertificateFile /etc/letsencrypt/live/znc.example.com/fullchain.pem | |||
SSLCertificateKeyFile /etc/letsencrypt/live/znc.example.com/privkey.pem | |||
</VirtualHost> | |||
</IfModule> | |||
</pre> | |||
==== As a Subdirectory ==== | |||
* You must set <code>URIPrefix</code> of the Listener in ZNC to the target location (<code>/znc/</code> in this example) | |||
* The ZNC web control panel can be accessed using (in this case) <code>https://znc.example.com/znc/</code> | |||
<pre> | |||
<IfModule mod_ssl.c> | |||
<VirtualHost *:443> | |||
ServerName znc.example.com | |||
ServerAdmin webmaster@localhost | |||
DocumentRoot /var/www/html/znc | |||
ErrorLog ${APACHE_LOG_DIR}/znc-error.log | |||
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined | |||
Include /etc/letsencrypt/options-ssl-apache.conf | |||
<Location /znc> | |||
ProxyPass http://localhost:4447/znc | |||
ProxyPassReverse http://localhost:4447/znc | |||
</Location> | |||
SSLCertificateFile /etc/letsencrypt/live/znc.example.com/fullchain.pem | |||
SSLCertificateKeyFile /etc/letsencrypt/live/znc.example.com/privkey.pem | |||
</VirtualHost> | |||
</IfModule> | |||
</pre> | |||
Latest revision as of 17:53, 8 May 2024
About Reverse Proxies
While ZNC is a fantastic bouncer, in many situations it can be beneficial to utilize a reverse proxy in front of it for features such as:
- Subdomains
- Tighter control of SSL ciphers and protocols
- ECDH support
- SSL session caching
- SSL stapling
- Compression
Notes
TrustedProxymust be set in your configuration for web access logs to reflect actual addresses instead of the reverse proxy address (127.0.0.1/::1):
TrustedProxy = 127.0.0.1 TrustedProxy = ::1
Nginx
Note: If you plan on utilizing Nginx for IRC in conjunction with HTTP/HTTPS, the port number (or address) of the two services must be different.
HTTP
As a Subdomain
server {
listen 80;
listen [::]:80;
# To listen on a specific address only:
# listen 192.0.2.1:80;
# listen [2001:db8::192:0:2:1]:80;
server_name znc.example.test;
access_log /var/log/nginx/znc.example.test/znc-access.log;
error_log /var/log/nginx/znc.example.test/znc-error.log;
location / {
proxy_pass http://[::1]:6667/;
# For IPv4 loopback (there's almost no reason to do this)
# proxy_pass http://127.0.0.1:6667/;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
As a Subdirectory
Note:
- There is intentionally no
/after the port number - You must set
URIPrefixof the Listener in ZNC to the target location (/znc/in this example)
server {
...
location /znc/ {
proxy_pass http://[::1]:6667;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
On most distributions this would be put in /etc/nginx/conf.d/znc.example.test.conf .
HTTPS
This is a basic configuration utilizing Diffie Hellman key exchange:
server {
listen 7001 ssl http2;
listen [::]:7001 ssl http2;
# To listen on a specific address only:
# listen 192.0.2.1:7001 ssl http2;
# listen [2001:db8::192:0:2:1]:7001 ssl http2;
server_name znc.example.test;
access_log /var/log/nginx/znc.example.test/znc_ssl-access.log;
error_log /var/log/nginx/znc.example.test/znc_ssl-error.log;
# SSL options
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
ssl_certificate /etc/letsencrypt/live/znc.example.test/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/znc.example.test/privkey.pem;
ssl_dhparam /etc/letsencrypt/live/znc.example.test/dhparam.pem;
ssl_trusted_certificate /etc/letsencrypt/live/znc.example.test/chain.pem;
location / {
proxy_pass http://[::1]:7001$uri;
# For IPv4 loopback (there's almost no reason to do this)
# proxy_pass http://127.0.0.1:7001$uri;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}
On most distributions this would be put in /etc/nginx/conf.d/znc.example.test.conf .
IRC
Nginx has a directive separate from http called stream for protocols other than HTTP. We can utilize this to allow nginx to act as a reverse proxy for ZNC:
upstream znc {
server [::1]:7000;
# For IPv4 loopback (there's almost no reason to do this)
# server 127.0.0.1:7000;
}
server {
listen 7000 ssl;
listen [::]:7000 ssl;
# To listen on a specific address only:
# listen 192.0.2.1:7000 ssl;
# listen [2001:db8::192:0:2:1]:7000 ssl;
# SSL options
ssl_certificate /etc/letsencrypt/live/znc.example.test/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/znc.example.test/privkey.pem;
ssl_dhparam /etc/letsencrypt/live/znc.example.test/dhparam.pem;
ssl_trusted_certificate /etc/letsencrypt/live/znc.example.test/chain.pem;
proxy_pass znc;
}
On most distributions these would be put in /etc/nginx/conf.d/znc.example.test.stream .
Additional Configuration Abilities
Nginx has many configuration options that can enhance the behavior of both the ZNC web interface and IRC, so the http or server nginx directive options below only demonstrate the most common portions of them:
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
server_tokens off;
# Compression
gzip on;
gzip_comp_level 9;
gzip_types application/javascript application/vnd.ms-fontobject application/x-font-otf application/x-font-ttf application/x-font-woff image/jpg image/png image/svg image/x-icon text/css;
###############
# SSL options #
###############
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:DHE-DSS-AES256-GCM-SHA384:DHE-DSS-AES256-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256;
ssl_ecdh_curve secp384r1;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_session_cache shared:https:15m;
ssl_session_timeout 15m;
# Stapling
ssl_stapling on;
ssl_stapling_verify on;
resolver 1.1.1.1 8.8.8.8 [2606:4700:4700::1111] [2001:4860:4860::8888];
lighttpd
HTTP
$HTTP["host"] =~ "^(sub\.domain\.com)$" {
proxy.server = ( "" => ( ( "host" => "127.0.0.1", "port" => 6667 ) ) )
}
Traefik
It is possible to run ZNC as a docker container, and use Traefik to provide proxying services for this. The IRC port needs to be separated from the web interface port to achieve this.
Traefik setup
Traefik needs to be configured to listen on a specific port for IRC access to ZNC. In this example, I'm using port 7000 for 'web' based access, and 7001 for 'IRC' access. This can be done in docker-compose as follows:
version: "3.5"
networks:
default:
name: traefik
services:
traefik:
image: "traefik:v2.3"
command:
--entryPoints.web.address=:7000
--entryPoints.irc.address=:7001
--providers.docker=true
ports:
- "7000:7000"
- "7001:7001"
ZNC setup
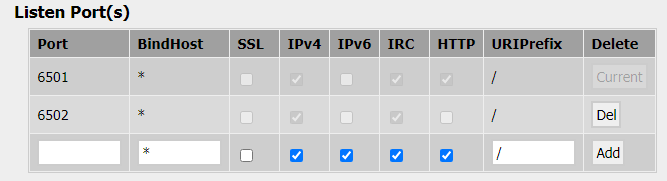
ZNC also needs to be configured to allow a separate port for IRC access. In this example, I'm using port 6501 for web access, and 6502 for IRC access. This is configured as follows:
The ZNC docker container then needs to be configured with appropriate labels to configure traefik to send traffic to it. This can be done in docker-compose as follows (in this case, the host name 'znc.example.com' is being used to access the ZNC service):
---
version: "3.5"
networks:
traefik:
external: true
default:
name: znc
services:
znc:
image: znc
container_name: znc
volumes:
- ./zncconfig:/znc-data
networks:
- default
- traefik
ports:
- 6501:6501
- 6502:6502
restart: unless-stopped
labels:
- "traefik.enable=true"
- "traefik.http.routers.zncweb.rule=Host(`znc.example.com`)"
- "traefik.http.routers.zncweb.tls=true"
- "traefik.http.routers.zncweb.entryPoints=web"
- "traefik.http.services.zncweb.loadbalancer.server.port=6501"
- "traefik.tcp.routers.zncirc.rule=HostSNI(`znc.example.com`)"
- "traefik.tcp.routers.zncirc.tls=true"
- "traefik.tcp.routers.zncirc.entryPoints=irc"
- "traefik.tcp.services.zncirc.loadbalancer.server.port=6502"
- "traefik.docker.network=traefik"
IRC client setup
All that is required then is to configure your IRC client to connect securely to 'znc.example.com' on port 7001, with SSL enabled. Traefik will then provide the appropriate certificate for the connection, and pass traffic to port 6502 on the ZNC container.
ZNC web control panel
The ZNC web control panel can be accessed using (in this case) https://znc.example.com:7000/
Caddy
Caddy is an extensible, cross-platform, open-source web server written in Go, with automatic TLS certificate provisioning.
Caddy only supports reverse proxying for HTTP out of the box, but the caddy-l4 plugin allows Caddy to proxy arbitrary streams, which makes it useful for ZNC. When using Caddy in this mode, the web control panel and IRC can be served from a single port.
Build Caddy with the caddy-l4 plugin by following the directions in caddy-l4's README.
caddy-l4 is configured by adding a `layer4` object to the `apps` object of a JSON Caddy configuration, like the one below. Note that the comments must be removed.
{
"apps": {
"layer4": {
"servers": {
"znc": {
"listen": [
":1337" // Caddy will listen on this interface
],
"routes": [
{
"handle": [
{
// Terminate TLS
"handler": "tls",
"connection_policies": [
{
"alpn": [
// Caddy always tries to negotiate HTTP/2 by default,
// which ZNC's web interface doesn't support, so we need
// to override the default protocol list
"http/1.1",
"http/1.0"
],
// Some IRC clients don't support SNI negotiation, so you
// need to tell Caddy which certificate to send
"default_sni": "your.hostname.com"
}
]
},
{
// Forward cleartext to ZNC
"handler": "proxy",
"upstreams": [
{
"dial": [
"localhost:2337" // The address where ZNC is listening
]
}
]
}
]
}
]
}
}
}
}
}
Apache
- You need the
proxy_httpandrewritemodules to be enabled. On Ubuntu you can doa2enmod proxy_http rewriteand then restart yor Apache instance.
HTTP
As a Subdomain
- The ZNC web control panel can be accessed using (in this case)
http://znc.example.com/
<VirtualHost *:80>
ServerName znc.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/znc
ErrorLog ${APACHE_LOG_DIR}/znc-error.log
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined
<Location />
ProxyPass http://localhost:1337/
ProxyPassReverse http://localhost:1337/
</Location>
</VirtualHost>
As a Subdirectory
- You must set
URIPrefixof the Listener in ZNC to the target location (/znc/in this example) - The ZNC web control panel can be accessed using (in this case)
http://znc.example.com/znc/
<VirtualHost *:80>
ServerName znc.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/znc
ErrorLog ${APACHE_LOG_DIR}/znc-error.log
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined
<Location /znc>
ProxyPass http://localhost:1337/znc
ProxyPassReverse http://localhost:1337/znc
</Location>
</VirtualHost>
HTTPS
As a Subdomain
- The ZNC web control panel can be accessed using (in this case)
https://znc.example.com/
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName znc.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/znc
ErrorLog ${APACHE_LOG_DIR}/znc-error.log
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined
Include /etc/letsencrypt/options-ssl-apache.conf
<Location />
ProxyPass http://localhost:4447/
ProxyPassReverse http://localhost:4447/
</Location>
SSLCertificateFile /etc/letsencrypt/live/znc.example.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/znc.example.com/privkey.pem
</VirtualHost>
</IfModule>
As a Subdirectory
- You must set
URIPrefixof the Listener in ZNC to the target location (/znc/in this example) - The ZNC web control panel can be accessed using (in this case)
https://znc.example.com/znc/
<IfModule mod_ssl.c>
<VirtualHost *:443>
ServerName znc.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/znc
ErrorLog ${APACHE_LOG_DIR}/znc-error.log
CustomLog ${APACHE_LOG_DIR}/znc-access.log combined
Include /etc/letsencrypt/options-ssl-apache.conf
<Location /znc>
ProxyPass http://localhost:4447/znc
ProxyPassReverse http://localhost:4447/znc
</Location>
SSLCertificateFile /etc/letsencrypt/live/znc.example.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/znc.example.com/privkey.pem
</VirtualHost>
</IfModule>